Difference between revisions of "Configure Asterisk TLS"
(Created page with '=Description= MOR supports TLS connection in order to encrypt signaling (SIP) traffic, however to use this functionality we need to generate certificates and setup both server an…') |
|||
| (5 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
=Description= | =Description= | ||
MOR supports TLS connection in order to encrypt signaling (SIP) traffic | MOR supports TLS connection in order to encrypt signaling (SIP) traffic. | ||
<br> | |||
To use this functionality you need to generate certificates and setup both server and end-client. | |||
<br> | |||
The default port for TLS is 5061, but you can set any other port, for example: tlsbindaddr=192.168.0.149:5099. | |||
<br> | |||
This functionality can be used as SIP TLS listener as it support SIP TLS with 5061 (Encrypted SIP). | |||
<br> | |||
This guide will explain how to configure TLS. | |||
<br><br> | <br><br> | ||
=Setup= | =Setup= | ||
In order to use TLS, certificates have to be setup on server side (MOR server) and client side (softphone, pbx, etc). | In order to use TLS, certificates have to be setup on server side (MOR server) and client side (softphone, pbx, etc). | ||
<br><br> | <br><br> | ||
== | ==Enable TLS on Asterisk== | ||
Certificates can be generated either for domain name or IP address. In this guide we will generate certificates for IP addresses and will assume (as example) that server IP address is 192.168.0.149, while client IP address is 192.168.0.130. To setup certificates, we will use ast_tls_cert helper script which is available in /usr/src/asterisk/contrib/scripts directory. | Certificates can be generated either for domain name or IP address. In this guide we will generate certificates for IP addresses and will assume (as example) that server IP address is 192.168.0.149, while client IP address is 192.168.0.130. To setup certificates, we will use ast_tls_cert helper script which is available in /usr/src/asterisk/contrib/scripts directory. | ||
| Line 20: | Line 29: | ||
tlscipher=ALL | tlscipher=ALL | ||
tlsclientmethod=tlsv1 | tlsclientmethod=tlsv1 | ||
#tlsbindaddr=192.168.0.149:5070 #if custom port is needed | |||
#externtlsport=5070 #if Asterisk is behind NAT and custom port is needed | |||
#tlsdontverifyserver=yes #when self-signed certificates are used, client side key is needed. This allows clients not to use client side keys. | |||
Once new configuration is saved, restart asterisk: | Once new configuration is saved, restart asterisk: | ||
service asterisk restart | service asterisk restart | ||
==Create key for Client== | |||
In MOR GUI Device settings, set checkbox to TLS in Advanced section Transport line: | |||
<br><br> | <br><br> | ||
[[File:TLS_zoiper0.png]] | [[File:TLS_zoiper0.png]] | ||
| Line 30: | Line 43: | ||
generate key for device: | |||
cd /usr/src/asterisk/contrib/scripts/ | cd /usr/src/asterisk/contrib/scripts/ | ||
./ast_tls_cert -m client -c /etc/asterisk/keys/ca.crt -k /etc/asterisk/keys/ca.key -C 192.168.0.130 -d /etc/asterisk/keys -o clientcert | ./ast_tls_cert -m client -c /etc/asterisk/keys/ca.crt -k /etc/asterisk/keys/ca.key -C 192.168.0.130 -d /etc/asterisk/keys -o clientcert | ||
Enter same passphrase you entered in previous command. Also, do not forget to replace 192.168.0.130 with client actual IP or domain name. | Enter same passphrase you entered in previous command. Also, do not forget to replace 192.168.0.130 with client actual IP or domain name. | ||
<br><br> | <br><br> | ||
==Setup On Client== | |||
==Setup On Client-side== | |||
In this guide we will show how to configure certificates for Zoiper softphone. Every softphone or PBX configuration is different, so you will need to consult documentation if you do not use Zoiper. | In this guide we will show how to configure certificates for Zoiper softphone. Every softphone or PBX configuration is different, so you will need to consult documentation if you do not use Zoiper. | ||
Latest revision as of 07:31, 26 November 2021
Description
MOR supports TLS connection in order to encrypt signaling (SIP) traffic.
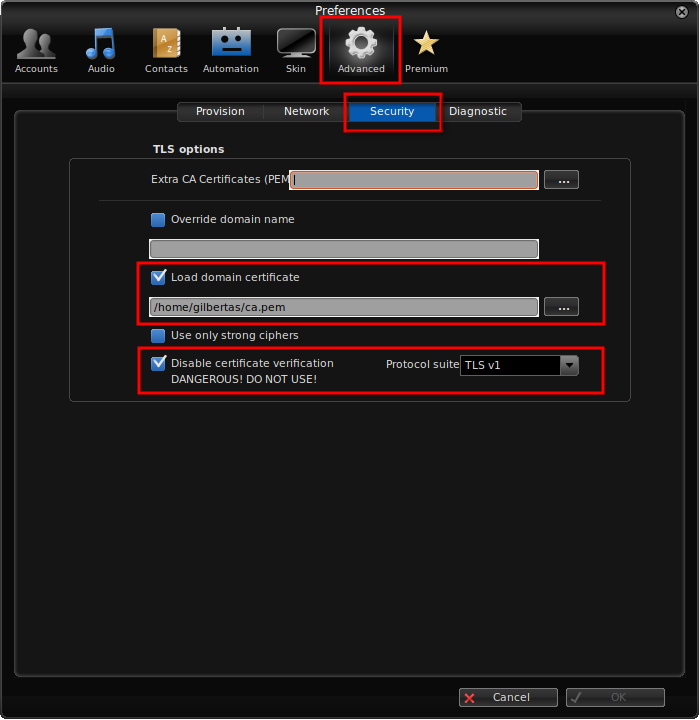
To use this functionality you need to generate certificates and setup both server and end-client.
The default port for TLS is 5061, but you can set any other port, for example: tlsbindaddr=192.168.0.149:5099.
This functionality can be used as SIP TLS listener as it support SIP TLS with 5061 (Encrypted SIP).
This guide will explain how to configure TLS.
Setup
In order to use TLS, certificates have to be setup on server side (MOR server) and client side (softphone, pbx, etc).
Enable TLS on Asterisk
Certificates can be generated either for domain name or IP address. In this guide we will generate certificates for IP addresses and will assume (as example) that server IP address is 192.168.0.149, while client IP address is 192.168.0.130. To setup certificates, we will use ast_tls_cert helper script which is available in /usr/src/asterisk/contrib/scripts directory.
cd /usr/src/asterisk/contrib/scripts/ ./ast_tls_cert -d /etc/asterisk/keys -C 192.168.0.149 -o morserver
ast_tls_cert script will ask to enter password (use randomly generated strong password and repeat each time it will ask for it) and will generate certificates in /etc/asterisk/keys directory.
Once certificates are generated, it is time to update /etc/asterisk/sip.conf configuration. We need to add the following lines in sip.conf (remember to replace 192.168.0.149 with your actual MOR server IP).
tlsenable=yes tlsbindaddr=192.168.0.149 tlscertfile=/etc/asterisk/keys/morserver.pem tlscafile=/etc/asterisk/keys/ca.crt tlscipher=ALL tlsclientmethod=tlsv1 #tlsbindaddr=192.168.0.149:5070 #if custom port is needed #externtlsport=5070 #if Asterisk is behind NAT and custom port is needed #tlsdontverifyserver=yes #when self-signed certificates are used, client side key is needed. This allows clients not to use client side keys.
Once new configuration is saved, restart asterisk:
service asterisk restart
Create key for Client
In MOR GUI Device settings, set checkbox to TLS in Advanced section Transport line:
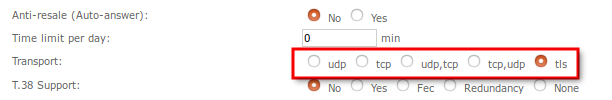
generate key for device:
cd /usr/src/asterisk/contrib/scripts/ ./ast_tls_cert -m client -c /etc/asterisk/keys/ca.crt -k /etc/asterisk/keys/ca.key -C 192.168.0.130 -d /etc/asterisk/keys -o clientcert
Enter same passphrase you entered in previous command. Also, do not forget to replace 192.168.0.130 with client actual IP or domain name.
Setup On Client-side
In this guide we will show how to configure certificates for Zoiper softphone. Every softphone or PBX configuration is different, so you will need to consult documentation if you do not use Zoiper.
- Copy the following files from MOR server to client PC where softphone is running:
/etc/asterisk/keys/clientcert.pem /etc/asterisk/keys/ca.crt
- Rename ca.crt to .pem extension, so that files would be named ca.pem and clientcert.pem
- Open Zoiper softphone, go to Settings->Preferences, go to global Advanced menu, then Security tab and load ca.pem domain certificate and set other options as shown in screenshot below:
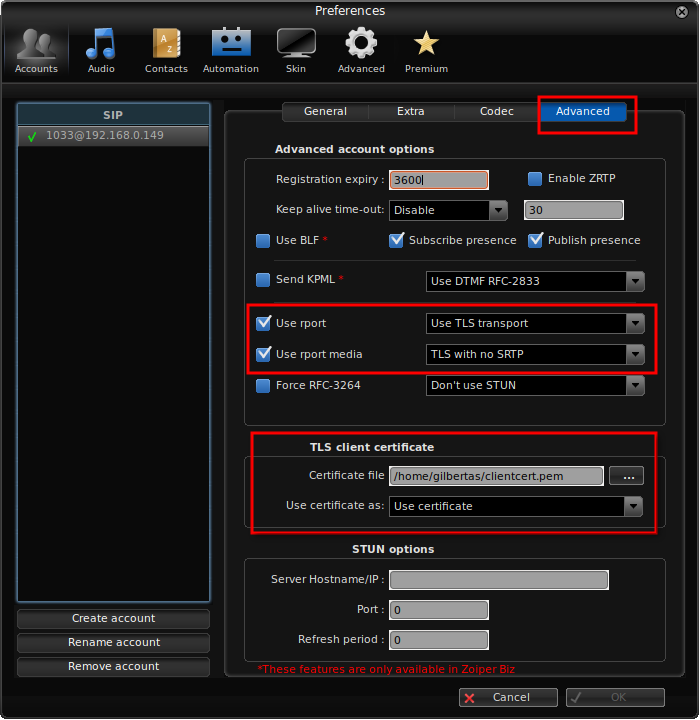
- Close previous configuration, go to Account settings, open Advanced section and load clientcert.pem certificate and set other options as shown in screenshot below:
- Make a test call and make a tcpdump between client IP and MOR server. You should see SIP traffic encrypted in TLS.
See Also
This guide is based on and more information can be found here:
https://wiki.asterisk.org/wiki/display/AST/Secure+Calling+Tutorial
https://ritcsec.wordpress.com/2017/05/19/voip-security-with-asterisk/