Difference between revisions of "How to be secure using MOR"
m |
|||
| (52 intermediate revisions by 6 users not shown) | |||
| Line 1: | Line 1: | ||
[[File:secure.png|right]] | |||
<br> | |||
= How to be secure using MOR = | = How to be secure using MOR = | ||
This guide will give you some hints where you could improve your MOR system security | This guide will give you some hints where you could improve your MOR system security | ||
| Line 11: | Line 13: | ||
# You must use different passwords for all types of services, for example '''MOR GUI''', '''ROOT''', phpmyadmin and stats passwords <u>must be different</u> | # You must use different passwords for all types of services, for example '''MOR GUI''', '''ROOT''', phpmyadmin and stats passwords <u>must be different</u> | ||
# When using SSH - please consider using [http://docs.redhat.com/docs/en-US/Red_Hat_Enterprise_Linux/6/html/Deployment_Guide/s2-ssh-configuration-keypairs.html SSH keys] instead of passwords. More information about SSH can be found [http://en.wikipedia.org/wiki/Secure_Shell here]. | # When using SSH - please consider using [http://docs.redhat.com/docs/en-US/Red_Hat_Enterprise_Linux/6/html/Deployment_Guide/s2-ssh-configuration-keypairs.html SSH keys] instead of passwords. More information about SSH can be found [http://en.wikipedia.org/wiki/Secure_Shell here]. | ||
# Change passwords regularly. Some guides how to do it: | |||
## [[I_want_to_change_a_root_password|Change root password]] | |||
## [[I_want_to_change_Eluna_stats_password|Change stats password]] | |||
## MOR GUI password - change it from user details | |||
# Change all default MOR passwords after installation. | |||
# [[Configuration_from_GUI#Security | Enable 2FA on login]] | |||
== Devices == | |||
# Make sure you carefully understand what each [[Device settings | device setting]] means. | |||
# Do not enable Insecure [http://www.voip-info.org/wiki/index.php?page=Asterisk+sip+insecure port + Invite], unless you understand what these settings mean! | |||
=== Device passwords === | |||
# Always create secure (as stated above) passwords for devices if you want to avoid loss. | |||
<br><br> | |||
== Multiple accounts registration == | |||
In order to prevent multiple accounts registration from the same user - you can implement an SMS based user verification using [[MOR_API_user_register|MOR API]] and a technique described [http://forum.kolmisoft.com/viewtopic.php?f=4&t=1648&p=9132#p9122 here]. | |||
<br><br> | <br><br> | ||
==MOR good practices== | ==MOR good practices== | ||
# It is '''recommended to disable public new user registrations''' or to be careful with: | # It is '''recommended to disable public new user registrations''' or to be careful with: | ||
| Line 17: | Line 40: | ||
### '''DO NOT put any initial balance''' - if you do so you will give money for calling for your new customers for free - such service is often abused and one or more users make a lot of of free account registrations to call for free. | ### '''DO NOT put any initial balance''' - if you do so you will give money for calling for your new customers for free - such service is often abused and one or more users make a lot of of free account registrations to call for free. | ||
### '''DO NOT MAKE USER POSTPAID''' - if you do so with public registrations enabled and you set any credit for that user (it can also be automatically applied from default user settings) - that user will be allowed to call for free and you risk that the unknown customer will not pay you. | ### '''DO NOT MAKE USER POSTPAID''' - if you do so with public registrations enabled and you set any credit for that user (it can also be automatically applied from default user settings) - that user will be allowed to call for free and you risk that the unknown customer will not pay you. | ||
### '''DO NOT GIVE ANY CREDIT in default user settings''' - if a credit is given and the user is postpaid - he is allowed to call till he reaches this limit. Very dangerous when being used with public user registrations. | |||
## | ## | ||
# Do not connect external PBX systems or at least ensure that they ARE SECURE. Please read more about this here: | # Do not connect external PBX systems or at least ensure that they ARE SECURE. Please read more about this [http://nerdvittles.com/?p=737 here], [http://www2.elastix.org/en/component/kunena/116-security/73040-how-to-change-the-default-asteriskuser-password.html here] and [http://blogtech.oc9.com/index.php?option=com_content&view=article&catid=18:securite--security&id=263:security2011-04&Itemid=6 here]. | ||
# Use [[Action_log|Action log]] feature in MOR to monitor suspicious users actions in MOR system. More information about [[Action_log|Action log]] can be found [[Action_log|here]]. | # Use [[Action_log|Action log]] feature in MOR to monitor suspicious users actions in MOR system. Keep an eye on '''Hacking attempt''' messages here - they indicate that the user is trying to access MOR GUI places/features which are not allowed for him to use. More information about [[Action_log|Action log]] can be found [[Action_log|here]]. | ||
# Use Admin account protection by IP: [[Unauthorized IP Address]] | |||
<br><br> | <br><br> | ||
| Line 25: | Line 50: | ||
===[[Monitorings_Addon|MOR Monitorings Addon]]=== | ===[[Monitorings_Addon|MOR Monitorings Addon]]=== | ||
[[Monitorings_Addon|Monitorings Addon]] addon will protect your from high money losses. More information about this addon can be found [[Monitorings_Addon|here]]. | [[Monitorings_Addon|Monitorings Addon]] addon will protect your from high money losses. More information about this addon can be found [[Monitorings_Addon|here]]. | ||
<br><br> | |||
===Fail2Ban=== | ===Fail2Ban=== | ||
[[Fail2Ban_installation|Fail2Ban]] is installed by default in MOR systems and protects | [[Fail2Ban_installation|Fail2Ban]] is installed by default in MOR systems and by using following rules protects server against brute force attacks and suspicious activity: | ||
* | * ssh-iptables - blocks IP which enters incorrect password 3 times in 10 minutes. Automatically unblocked after 10 minutes. | ||
* Asterisk - | * asterisk-iptables - blocks IP which tries SIP registration with wrong password 5 times in 10 minutes. Automatically unblocked after 10 minutes. | ||
* ast-cli-attck - blocks IP which sends any SIP packet from sipcli, sipvicious, sip-scan, sipsak, sundayddr, friendly-scanner, iWar, CSipSimple, SIVuS, Gulp, sipv, smap, friendly-request, VaxIPUserAgent, VaxSIPUserAgent, siparmyknife or Test Agent tool. Blocked permanently, no automatic unblock. | |||
* asterisk-manager - blocks IP if it tries to connect Asterisk Manager Interface and is not authorized to do that. Blocked permanently, no automatic unblock. | |||
* ast-hgc-200 - blocks IP who attempts to send unauthorized call (HGC 200) 20 times in 10 minutes. Blocked permanently, no automatic unblock. | |||
* mor_api - blocks IP which tries to use MOR API with wrong authentication details. Blocked permanently, no automatic unblock. | |||
* mor_ddos - block IP which tries incorrect and suspicious URLs 20 times in 10 minutes. Automatically unblocked after 1 hour. | |||
More information about Fail2Ban can be found [[Fail2Ban_installation|here]] | Information how to override default Kolmisoft Fail2Ban configuration can be found [[Extending Fail2Ban configuration|here]]. | ||
===Iptables=== | |||
More information about Fail2Ban can be found [[Fail2Ban|here]] and [[Fail2Ban_installation|here]]. | |||
<br><br> | |||
===[http://linux.die.net/man/8/iptables Iptables]=== | |||
It is a default Linux firewall and is installed by default in all MOR systems. Although additional configuration is needed in order it would protect you: | It is a default Linux firewall and is installed by default in all MOR systems. Although additional configuration is needed in order it would protect you: | ||
* Configure iptables that it would accept connections only to ports required for MOR system to work. More information about these ports can be found [[Ports_which_should_be_opened|here]]. | * Configure iptables that it would accept connections only to ports required for MOR system to work. More information about these ports can be found [[Ports_which_should_be_opened|here]]. | ||
* Allow connections to SSH (default TCP Port: 22) only from support.kolmisoft.com and systems you trust. | * Allow connections to SSH (default TCP Port: 22) only from support.kolmisoft.com and systems you trust. | ||
* If MOR GUI is not required for your business model - you can block access to it too (Default TCP ports: 80/443). Only remember to allow access to it from support.kolmisoft.com and the systems you trust. | * If MOR GUI is not required for your business model - you can block access to it too (Default TCP ports: 80/443). Only remember to allow access to it from support.kolmisoft.com and the systems you trust. | ||
<br><br> | |||
<br><br> | |||
==Does Fail2ban block calls with hang up cause code 200?== | |||
By default Fail2Ban blocks calls (IP address sending those calls) with HGC 200 when there are 20 or more such attempts / minute - it is a safe limit which should never be reached by normal users. This behavious can be easy adjusted. See [[Extending_Fail2Ban_configuration|this guide]] how to achieve this. | |||
See also: | |||
http://wiki.kolmisoft.com/index.php/Lots_of_calls_made_by_System_Admin_user | |||
<br><br> | |||
==Services== | |||
* Apache (httpd) - you must use SSL in order you and your users could surf MOR GUI safely. More information about installing SSL can be found [[Setting_up_https_secure_connection|here]]. | |||
* Asterisk - do not connect external PBX systems or at least ensure that they ARE SECURE. Please read more about known insecure PBX systems [http://nerdvittles.com/?p=737 here], [http://www2.elastix.org/en/component/kunena/116-security/73040-how-to-change-the-default-asteriskuser-password.html here] and [http://blogtech.oc9.com/index.php?option=com_content&view=article&catid=18:securite--security&id=263:security2011-04&Itemid=6 here]. | |||
* SSH - you can go even further securing the SSH - you can limit the number of allowed SSH connections per minute. For more information please check this [http://wiki.centos.org/HowTos/Network/SecuringSSH#head-a296ec93e31637aa349538be07b37f67d836688a guide]. | |||
* MySQL - [http://stackoverflow.com/questions/8014358/how-to-run-command-mysqladmin-flush-hosts-on-amazon-rds-database-server-instan read here] why you don't need to use Fail2Ban in order to block unsuccessful login attempts. | |||
<br><br> | |||
==Various security related guides== | |||
* [[How_to_block_someone%27s_IP | How to block/unblock someone's IP]] | |||
* [[Blocked_Countries | How to block Countries]] | |||
<br><br> | |||
==Very advanced techniques for highly technically skilled people== | |||
For these techniques Kolmisoft does not provide any support. | |||
* Port knocking (can be used for SSH or GUI access if it is not used publicly). More information about this technique can be found [http://www.portknocking.org/ here]. | |||
* Intrusion prevention systems: [http://www.cisco.com/en/US/products/ps5729/Products_Sub_Category_Home.html Cisco] [http://www.openinfosecfoundation.org/ Suricata] | |||
<br><br> | |||
==Protection against Brute-force attacks== | |||
If you try to login to MOR system unsuccesfully 3 times in a row (via GUI or API) you will have to wait 10 seconds to login again. | |||
Note that 10 seconds blocking is set to the '''IP''', so everyone who are trying to access MOR System from the same '''IP''' will have to wait for 10 seconds. | |||
[[File:Login bad.png]] | |||
<br><br> | |||
== Block Countries == | |||
Deny/Allow access only from specified Countries, using [[Blocked Countries]] functionality | |||
<br><br> | |||
== Alerts == | |||
Use [[Alerts]] functionality to prevent the hacking attempts. | |||
<br><br> | |||
=See also= | |||
*[[Secure email]] | |||
* [http://blog.kolmisoft.com/sip-attack-friendly-scanner/ SIP Attack: Friendly Scanner] | |||
Latest revision as of 11:30, 5 December 2022
How to be secure using MOR
This guide will give you some hints where you could improve your MOR system security
Passwords
- Never give passwords to people you do not trust
- Use only secure passwords:
- Your passwords must be at least 12 symbols length
- Your passwords must contain letters (a-z)
- Your passwords must contain numbers (0-9)
- Your passwords must contain special characters (!@#$%^&*() and so on..)
- You must use different passwords for all types of services, for example MOR GUI, ROOT, phpmyadmin and stats passwords must be different
- When using SSH - please consider using SSH keys instead of passwords. More information about SSH can be found here.
- Change passwords regularly. Some guides how to do it:
- Change root password
- Change stats password
- MOR GUI password - change it from user details
- Change all default MOR passwords after installation.
- Enable 2FA on login
Devices
- Make sure you carefully understand what each device setting means.
- Do not enable Insecure port + Invite, unless you understand what these settings mean!
Device passwords
- Always create secure (as stated above) passwords for devices if you want to avoid loss.
Multiple accounts registration
In order to prevent multiple accounts registration from the same user - you can implement an SMS based user verification using MOR API and a technique described here.
MOR good practices
- It is recommended to disable public new user registrations or to be careful with:
- Default user settings - it is common for new users to do these mistakes:
- DO NOT put any initial balance - if you do so you will give money for calling for your new customers for free - such service is often abused and one or more users make a lot of of free account registrations to call for free.
- DO NOT MAKE USER POSTPAID - if you do so with public registrations enabled and you set any credit for that user (it can also be automatically applied from default user settings) - that user will be allowed to call for free and you risk that the unknown customer will not pay you.
- DO NOT GIVE ANY CREDIT in default user settings - if a credit is given and the user is postpaid - he is allowed to call till he reaches this limit. Very dangerous when being used with public user registrations.
- Default user settings - it is common for new users to do these mistakes:
- Do not connect external PBX systems or at least ensure that they ARE SECURE. Please read more about this here, here and here.
- Use Action log feature in MOR to monitor suspicious users actions in MOR system. Keep an eye on Hacking attempt messages here - they indicate that the user is trying to access MOR GUI places/features which are not allowed for him to use. More information about Action log can be found here.
- Use Admin account protection by IP: Unauthorized IP Address
Additional software to increase MOR system security
MOR Monitorings Addon
Monitorings Addon addon will protect your from high money losses. More information about this addon can be found here.
Fail2Ban
Fail2Ban is installed by default in MOR systems and by using following rules protects server against brute force attacks and suspicious activity:
- ssh-iptables - blocks IP which enters incorrect password 3 times in 10 minutes. Automatically unblocked after 10 minutes.
- asterisk-iptables - blocks IP which tries SIP registration with wrong password 5 times in 10 minutes. Automatically unblocked after 10 minutes.
- ast-cli-attck - blocks IP which sends any SIP packet from sipcli, sipvicious, sip-scan, sipsak, sundayddr, friendly-scanner, iWar, CSipSimple, SIVuS, Gulp, sipv, smap, friendly-request, VaxIPUserAgent, VaxSIPUserAgent, siparmyknife or Test Agent tool. Blocked permanently, no automatic unblock.
- asterisk-manager - blocks IP if it tries to connect Asterisk Manager Interface and is not authorized to do that. Blocked permanently, no automatic unblock.
- ast-hgc-200 - blocks IP who attempts to send unauthorized call (HGC 200) 20 times in 10 minutes. Blocked permanently, no automatic unblock.
- mor_api - blocks IP which tries to use MOR API with wrong authentication details. Blocked permanently, no automatic unblock.
- mor_ddos - block IP which tries incorrect and suspicious URLs 20 times in 10 minutes. Automatically unblocked after 1 hour.
Information how to override default Kolmisoft Fail2Ban configuration can be found here.
More information about Fail2Ban can be found here and here.
Iptables
It is a default Linux firewall and is installed by default in all MOR systems. Although additional configuration is needed in order it would protect you:
- Configure iptables that it would accept connections only to ports required for MOR system to work. More information about these ports can be found here.
- Allow connections to SSH (default TCP Port: 22) only from support.kolmisoft.com and systems you trust.
- If MOR GUI is not required for your business model - you can block access to it too (Default TCP ports: 80/443). Only remember to allow access to it from support.kolmisoft.com and the systems you trust.
Does Fail2ban block calls with hang up cause code 200?
By default Fail2Ban blocks calls (IP address sending those calls) with HGC 200 when there are 20 or more such attempts / minute - it is a safe limit which should never be reached by normal users. This behavious can be easy adjusted. See this guide how to achieve this.
See also:
http://wiki.kolmisoft.com/index.php/Lots_of_calls_made_by_System_Admin_user
Services
- Apache (httpd) - you must use SSL in order you and your users could surf MOR GUI safely. More information about installing SSL can be found here.
- Asterisk - do not connect external PBX systems or at least ensure that they ARE SECURE. Please read more about known insecure PBX systems here, here and here.
- SSH - you can go even further securing the SSH - you can limit the number of allowed SSH connections per minute. For more information please check this guide.
- MySQL - read here why you don't need to use Fail2Ban in order to block unsuccessful login attempts.
Very advanced techniques for highly technically skilled people
For these techniques Kolmisoft does not provide any support.
- Port knocking (can be used for SSH or GUI access if it is not used publicly). More information about this technique can be found here.
- Intrusion prevention systems: Cisco Suricata
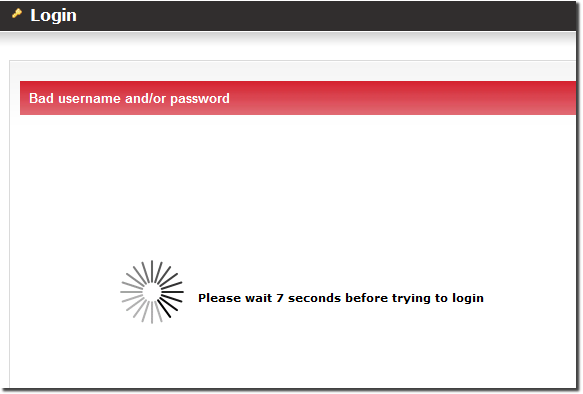
Protection against Brute-force attacks
If you try to login to MOR system unsuccesfully 3 times in a row (via GUI or API) you will have to wait 10 seconds to login again.
Note that 10 seconds blocking is set to the IP, so everyone who are trying to access MOR System from the same IP will have to wait for 10 seconds.
Block Countries
Deny/Allow access only from specified Countries, using Blocked Countries functionality
Alerts
Use Alerts functionality to prevent the hacking attempts.