Difference between revisions of "Setting up https secure connection"
m (→Installing SSL) |
|||
| (46 intermediate revisions by 7 users not shown) | |||
| Line 1: | Line 1: | ||
= Installing SSL = | = Installing SSL = | ||
In new MOR (starting from X14) and M2 installs, SSL with self-signed certificate is preconfigured (using external sever IP). | |||
If you have older MOR and M2 installations, and SSL was not configured previously, you can configure self-signed certificate in MOR/M2 by running the following script. Script is tested and ready to use: | |||
For MOR: | |||
svn update /usr/src/mor | |||
/usr/src/mor/MOR_version/gui/ssl_install.sh | |||
For M2: | |||
svn update /usr/src/m2 | |||
/usr/src/m2/gui/ssl_install.sh | |||
And restart httpd service | |||
service httpd restart | |||
Clear browser cache before testing redirect. Otherwise it might not work. | |||
== Allow only https == | |||
If you would like your users to be automatically redirected to secure connection (https), add the line to /etc/httpd/conf.d/m2.conf so it would look like: | |||
<VirtualHost *:80> | |||
DocumentRoot /var/www/html | |||
<Directory /var/www/html> | |||
Allow from all | |||
</Directory> | |||
RailsBaseURI /billing | |||
<Directory /var/www/html/billing> | |||
Options -MultiViews | |||
</Directory> | |||
RailsEnv production | |||
Redirect permanent / https://www.example.com/ #Add this one. Put your hostname instead of www.example.com | |||
</VirtualHost> | |||
And restart httpd service | |||
service httpd restart | |||
Also change from http to https in cron actions: | |||
sed -i 's#http:#https:#' /etc/cron.d/*actions | |||
service crond restart | |||
<br><br> | |||
== Configure Domain Name == | |||
If you have domain name, replace IP_ADDRESS (which will be your external IP address) with your domain name and regenerate certification files with new information with command bellow: | |||
openssl req -new -newkey rsa:4096 -days 365 -nodes -x509 -keyout /etc/httpd/ssl/apache.key -out /etc/httpd/ssl/apache.crt | |||
Enter information as requested, in common name section please enter your domain name. | |||
And restart httpd service | |||
service httpd restart | service httpd restart | ||
== Cron Actions == | |||
If SSL redirection is enabled, ensure that hourly actions are able to access GUI internally: | |||
wget http://127.0.0.1/billing/callc/hourly_actions | |||
if it does not work, adjust domain or add --no-check-certificate like this: | |||
wget --no-check-certificate http://127.0.0.1/billing/callc/hourly_actions | |||
For https connection use: | |||
wget https://127.0.0.1/billing/callc/hourly_actions | |||
Or: | |||
wget --no-check-certificate https://127.0.0.1/billing/callc/hourly_actions | |||
Once command works, make same adjustments on /etc/cron.d/mor_hourly_actions, mor_daily_actions and mor_monthly_actions. | |||
'''!!!DO NOT TEST RUN daily AND monthly ACTIONS MANUALLY!!!''' just adjust cron files, save then and restart crond service. | |||
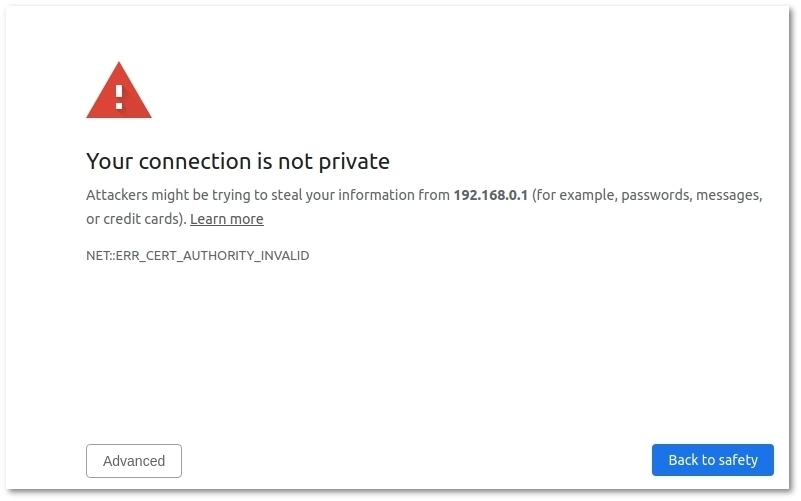
== Connection is not private Notification == | |||
When using self-signed certificate, you will get notification that your connection is not private. | |||
[[File:Privacy1.png]] | |||
To fix this, press '''Advanced''' and after - '''Proceed'''. You will see this message only once from same Browser/Computer. | |||
To avoid this message, you can buy certificates from SSL Providers. | |||
== Using your own certificates == | |||
Configuration may vary depending on SSL provider. As always, make backup of files before editing them, so you would be able to revert in case of failure. | |||
If you want to use SSL Provider's certificates, you have to update self-signed configuration which should be already installed in your server. | |||
Place certificate files somewhere in filesystem and update following lines in /etc/httpd/conf.d/ssl.conf with location of certificate files: | |||
SSLCertificateFile /etc/httpd/ssl/apache.crt | |||
SSLCertificateKeyFile /etc/httpd/ssl/apache.key | |||
SSLCertificateChainFile /etc/pki/tls/certs/server-chain.crt | |||
in same file, uncomment this line and set your domain: | |||
ServerName www.example.com:443 | |||
save changes. | |||
Set your domain instead of IP address in /etc/httpd/conf.d/mor_ssl.conf | |||
ServerName 1.2.3.4 | |||
save changes. | |||
Restart apache to apply changes: | |||
service httpd restart | |||
Check cron actions as described above. | |||
== | == Hardening SSL security == | ||
By default, old SSL/TLS protocols versions and ciphers are enabled which can cause security threats. To disable them, open /etc/httpd/conf.d/ssl.conf, find lines which starts with the following keywords - SSLProtocol, SSLCipherSuite. Comment them out and add following lines: | |||
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 | |||
SSLCipherSuite HIGH:!aNULL:!MD5:!3DES | |||
SSLHonorCipherOrder on | |||
Configuration with commented lines should look like this: | |||
# SSL Protocol support: | |||
# List the enable protocol levels with which clients will be able to | |||
# connect. Disable SSLv2 access by default: | |||
#SSLProtocol all -SSLv2 | |||
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 | |||
# SSL Cipher Suite: | |||
# List the ciphers that the client is permitted to negotiate. | |||
# See the mod_ssl documentation for a complete list. | |||
#SSLCipherSuite DEFAULT:!EXP:!SSLv2:!DES:!IDEA:!SEED:+3DES | |||
SSLCipherSuite HIGH:!aNULL:!MD5:!3DES | |||
SSLHonorCipherOrder on | |||
Restart httpd: | |||
service httpd restart | |||
If after this you having problems connecting, uncoment old values, comment new ones, and restart httpd again | |||
Revision as of 14:55, 20 January 2021
Installing SSL
In new MOR (starting from X14) and M2 installs, SSL with self-signed certificate is preconfigured (using external sever IP). If you have older MOR and M2 installations, and SSL was not configured previously, you can configure self-signed certificate in MOR/M2 by running the following script. Script is tested and ready to use:
For MOR:
svn update /usr/src/mor /usr/src/mor/MOR_version/gui/ssl_install.sh
For M2:
svn update /usr/src/m2 /usr/src/m2/gui/ssl_install.sh
And restart httpd service
service httpd restart
Clear browser cache before testing redirect. Otherwise it might not work.
Allow only https
If you would like your users to be automatically redirected to secure connection (https), add the line to /etc/httpd/conf.d/m2.conf so it would look like:
<VirtualHost *:80> DocumentRoot /var/www/html <Directory /var/www/html> Allow from all </Directory> RailsBaseURI /billing <Directory /var/www/html/billing> Options -MultiViews </Directory> RailsEnv production Redirect permanent / https://www.example.com/ #Add this one. Put your hostname instead of www.example.com </VirtualHost>
And restart httpd service
service httpd restart
Also change from http to https in cron actions:
sed -i 's#http:#https:#' /etc/cron.d/*actions service crond restart
Configure Domain Name
If you have domain name, replace IP_ADDRESS (which will be your external IP address) with your domain name and regenerate certification files with new information with command bellow:
openssl req -new -newkey rsa:4096 -days 365 -nodes -x509 -keyout /etc/httpd/ssl/apache.key -out /etc/httpd/ssl/apache.crt
Enter information as requested, in common name section please enter your domain name.
And restart httpd service
service httpd restart
Cron Actions
If SSL redirection is enabled, ensure that hourly actions are able to access GUI internally:
wget http://127.0.0.1/billing/callc/hourly_actions
if it does not work, adjust domain or add --no-check-certificate like this:
wget --no-check-certificate http://127.0.0.1/billing/callc/hourly_actions
For https connection use:
wget https://127.0.0.1/billing/callc/hourly_actions
Or:
wget --no-check-certificate https://127.0.0.1/billing/callc/hourly_actions
Once command works, make same adjustments on /etc/cron.d/mor_hourly_actions, mor_daily_actions and mor_monthly_actions.
!!!DO NOT TEST RUN daily AND monthly ACTIONS MANUALLY!!! just adjust cron files, save then and restart crond service.
Connection is not private Notification
When using self-signed certificate, you will get notification that your connection is not private.
To fix this, press Advanced and after - Proceed. You will see this message only once from same Browser/Computer. To avoid this message, you can buy certificates from SSL Providers.
Using your own certificates
Configuration may vary depending on SSL provider. As always, make backup of files before editing them, so you would be able to revert in case of failure.
If you want to use SSL Provider's certificates, you have to update self-signed configuration which should be already installed in your server.
Place certificate files somewhere in filesystem and update following lines in /etc/httpd/conf.d/ssl.conf with location of certificate files:
SSLCertificateFile /etc/httpd/ssl/apache.crt SSLCertificateKeyFile /etc/httpd/ssl/apache.key SSLCertificateChainFile /etc/pki/tls/certs/server-chain.crt
in same file, uncomment this line and set your domain:
ServerName www.example.com:443
save changes.
Set your domain instead of IP address in /etc/httpd/conf.d/mor_ssl.conf
ServerName 1.2.3.4
save changes.
Restart apache to apply changes:
service httpd restart
Check cron actions as described above.
Hardening SSL security
By default, old SSL/TLS protocols versions and ciphers are enabled which can cause security threats. To disable them, open /etc/httpd/conf.d/ssl.conf, find lines which starts with the following keywords - SSLProtocol, SSLCipherSuite. Comment them out and add following lines:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 SSLCipherSuite HIGH:!aNULL:!MD5:!3DES SSLHonorCipherOrder on
Configuration with commented lines should look like this:
# SSL Protocol support: # List the enable protocol levels with which clients will be able to # connect. Disable SSLv2 access by default: #SSLProtocol all -SSLv2 SSLProtocol all -SSLv2 -SSLv3 -TLSv1 # SSL Cipher Suite: # List the ciphers that the client is permitted to negotiate. # See the mod_ssl documentation for a complete list. #SSLCipherSuite DEFAULT:!EXP:!SSLv2:!DES:!IDEA:!SEED:+3DES SSLCipherSuite HIGH:!aNULL:!MD5:!3DES SSLHonorCipherOrder on
Restart httpd:
service httpd restart
If after this you having problems connecting, uncoment old values, comment new ones, and restart httpd again